3 Components of Application Security Management in 2024
As software eats the world, cybersecurity threats, including data breaches, cyber theft, and malicious attacks are on the rise. In Q1 2023, over six million data records were breached globally.1
This increases the need for Application Security Management (ASM) employs a multi-layered approach that includes securing development practices, security tools, and real-time security monitoring.
Though AppSec is critical to software security, it is a noisy domain with a wide range of categories and definitions. Explore below the approaches that contribute to application security management (ASM) (Figure 1), also called application security posture management (ASPM), throughout the software development lifecycle (SDLC).
What is Application Security Management (ASM)?
ASM is made up of these proactive application security measures which help mitigate vulnerabilities and cyberattacks:
- Risk-based security compliance which includes threat modeling and secure coding practices
- Application security testing including: static application security testing (SAST) and dynamic application security testing (DAST) and integrated application security testing (IAST) tools
- Advanced threat detection and response solutions: Security Analytics (SA) platforms relying and leverage capabilities of security information and event management (SIEM), including and differentiating further practices such as: Security orchestration, automation, and response (SOAR) extended detection and response (XDR), and user and entity behavior analytics (UEBA)
Why is ASM important?
The variety of tools available for web application security testing shows a focus on encryption and logging to prioritize speed. However, security teams struggle with this emphasis because market pressures often prioritize speed over thorough web application security testing, leading to vulnerabilities that attackers can exploit. This focus on speed can be detrimental, as the global average cost of a data breach in 2023 was USD 4.5 million. 2

Secure software development relies on protecting the source code (encryption, access control) and achieving high code coverage through testing (Figure 1).
Inadequate security testing can leave organizations exposed to significant financial repercussions.
Risk-based security compliance
Compliance standards act as a framework, mandating the implementation of security controls to protect sensitive data.
Compliance with security standards and regulations driven on information security management systems (ISMS) for developers to manage risks and mitigate vulnerabilities is essential for building trust, safeguarding reputation, ensuring data integrity, and protecting an organization’s financial well-being.
- These standards establish minimum security controls, promoting cyber hygiene practices and fostering a culture of continuous security improvement.
Compliance with global IT security standards and regulations enforces a baseline level of security controls, offering broader protection against diverse attack vectors. 3
Security-focused development practices (secure coding, threat modeling) proactively address vulnerabilities throughout the software development lifecycle (SDLC), mitigating data breaches and malicious attacks (Figure 2) by often requiring a risk-based approach. 4

What is threat modeling?
Dangers now include mutating software, advanced persistent threats (APT), insider threats, and software vulnerabilities around cloud-based computing services — more than antivirus software can handle.
Key steps involve:
- Defining critical assets: Identify and clearly define the data and systems essential for the organization’s operation.
- Mapping application interactions: Analyze how each application interacts with these assets, understanding its role in data access and manipulation.
- Building application security profiles: Create a security profile for each application, outlining its access controls and functionalities.
- Threat identification and prioritization: Systematically identify potential threats (e.g., unauthorized access, data breaches) and prioritize them based on likelihood and impact.
- Documenting incidents and responses: Record any adverse security events and the corresponding actions taken to mitigate them.
What is source code protection?
Measures taken to safeguard a program’s source code from unauthorized access, alteration, or theft. This includes:
- Digital security: Encryption and authentication procedures to restrict access and protect code confidentiality.
- Physical security: Limiting physical access to code repositories and development environments.
Code coverage: A metric reflecting the percentage of code executed during automated testing. It helps identify areas requiring additional testing and ensures code validation.
Application Security Testing (AST) for AppSec Management (ASM)
Application security testing (AST) is a crucial component of application security management (AppSec). During the software development process, developers leverage AST to identify and mitigate security vulnerabilities within new or updated applications.
Multi-faceted testing
Static Application Security Testing (SAST) tools scan application source code for security weaknesses in coding and design to identify vulnerabilities in the data flow and help you fix them before software release.
- Helps secure software by finding secrets like API keys accidentally left in code during development.
- Used early in the development stage, specifically; coding phase, code reviews and unit testing.
Dynamic Application Security Testing (DAST) tools evaluate the application’s behavior during runtime to identify vulnerabilities that may emerge during interaction.
In dynamic testing, also called black-box testing, software is tested without knowing its inner functions by simulating real-world attacks. It is used during the development stage and the test/QA stage.
Interactive Application Security Testing (IAST) software supports functional testing or QA efforts.
- IAST correlates scan results with findings from DAST and SAST scans.
- Enables streamlined issue categorization and rectification.
- Used during the development and test/QA stage focused on run-time of applications.
Software composition analysis SCA, also called open source software (OSS) security tools, safeguards applications by detecting vulnerabilities in open source components used in the code.
- Analyzes various sources (hashes, binaries) to identify these risks, ensuring overall application security.
- Ideally used throughout the development stage, offering monitoring and early detection of vulnerabilities in third-party components.
Revealed outcomes are fed back to developers, who fix identified vulnerabilities during development.
Advanced threat detection and response solutions
Security information and event management (SIEM) technology first emerged as a compliance reporting tool. Security analytics centralizes data and applies advanced analytics to empower security teams.
SIEM, and security analytics platforms are solutions that grants a comprehensive view of the threat landscape, facilitating the identification of both external attacks and insider threats and vulnerabilities before they have a chance to disrupt business operations.
What is Security information and event management (SIEM)?
SIEM solutions are mainly used to record and manage large volumes of security event data from an organization’s applications, devices, servers and users enabling security teams to detect and block attacks by leveraging real-time monitoring and data analysis.
Event correlation and analytics
Using advanced analytics to identify and understand intricate data patterns, event correlation provides insights to quickly locate and mitigate potential threats to business security.
They excel at managing vast amounts of security event data from diverse sources and facilitating real-time monitoring and analysis. This enhanced capability empowers security teams to proactively identify and potentially block attacks, moving beyond a purely compliance-driven approach.
Centralized threat assessment & alerting
- Centralized hub: consolidating security alerts from diverse sources. This approach facilitates review, analysis, and response actions by security teams.
- Predefined rules & anomaly detection: leverages predetermined rules configured by security teams to define potential threats and trigger corresponding alerts.
Additionally, the realization that SIEM data could transform raw information into security intelligence spurred the widespread adoption of SIEMs within Security Operations Center (SOC)s.
Security Analytics Platforms
Security analytics (SA) combines software, algorithms, and analytical processes to proactively identify potential threats to IT systems (Figure 4). It goes beyond basic detection to predict and prevent attacks. These platforms leverage data analysis to uncover insights and respond to potential cyberattacks. 5
Extracting Network Data
- Behavioral analytics: Security analytics platforms utilize behavioral machine learning or analytics techniques to analyze network traffic and user behavior data.
- Data ingestion and analysis: These platforms collect data from various sources (e.g., SIEM systems), normalize it for consistency, and then analyze it for patterns indicative of threats. Both real-time and historical data are used for comprehensive analysis.

Security analytics features
- Data integration: Security analytics tools can ingest data from SIEM systems and other security sources for analysis.
- UEBA (User and Entity Behavior Analytics): Analyzes user and entity activity to detect anomalies that might indicate compromised accounts or insider behavior.
- Automated and on-demand traffic analysis: Platforms offer both automated real-time analysis and the ability to perform on-demand analysis of network traffic for specific investigations.
- Threat intelligence integration: Security analytics can compare observed behavior patterns against known threat intelligence feeds, allowing for identification of potential attacks.
- Policy-based analytics: Security teams can configure the platform to monitor behavior against predefined security policies, enabling detection of policy violations.
SOAR as a response to SIEM limitations
Security orchestration, automation, and response (SOAR) platforms integrate diverse security tools, enabling unhindered data flow and a consolidated security posture. They automate repetitive tasks within incident and threat response workflows, offering a centralized hub for collaboration and communication.
The emergence of SOAR solutions can be attributed, in part, to the limitations of traditional SIEM tools. While SIEM excels at security information and event management, it often lacks robust orchestration, automation, and console functionalities. SOAR addresses this gap by adding these security-focused features:
- Orchestration: facilitates the orchestration of actions across various security tools, enabling a coordinated response to incidents.
- Automation: automates repetitive tasks within incident response workflows, improving efficiency and reducing human error.
- Centralized console: provides a central console for managing and monitoring all security operations, improving collaboration and situational awareness for security teams.
Capabilities of SIEM and Security Analytics Tools
Security information and event management (SIEM) and security analytics tools form a powerful combination for security operations. Here’s a breakdown of their key capabilities:
- Threat detection: Both SIEM and security analytics tools excel at threat detection.
- SIEM aggregates security event data from various sources, allowing for identification of suspicious activity patterns.
- Security analytics leverage advanced analytics techniques to detect anomalies that might indicate potential threats.
- Correlation and User Entity Behavior Analytics (UEBA): SIEM can correlate security events from different sources to identify potential threats that might not be evident from isolated events.
- Security analytics tools often incorporate UEBA functionalities, enabling analysis of user and entity behavior patterns to detect deviations indicative of compromised accounts, insider threats, or other security risks.
- Response integrations: Both SIEM and security analytics tools can integrate with security orchestration, automation and response (SOAR) platforms. This allows for automated responses to identified threats, streamlining incident response workflows.
- Security reporting and threat intelligence: SIEM and security analytics tools offer security reporting functionalities. Additionally, these tools can integrate with threat intelligence platforms (TIPs), providing access to continuously updated threat data that enriches threat detection capabilities.
XDR emerged to tackle the challenges of SIEM and Security Analytics
Extended Detection and Response (XDR) represents a significant advancement over endpoint detection and response (EDR) solutions. While EDR focuses primarily on endpoints, XDR functions as a unifying security analytics tool (Figure 5). It integrates security solutions that were not originally designed to work together providing a broader perspective, enabling optimized threat assessment and response across the entire security landscape, including business tools.

XDR Integration Capabilities
XDR security solutions demonstrate impressive integration capabilities, encompassing diverse security tools:
- Individual security tools: Antivirus software, UEBA (User and Entity Behavior Analytics), firewalls, etc.
- Layer-specific solutions: EDR (Endpoint Detection and Response), EPP (Endpoint Protection Platforms), NDR (Network Detection and Response), NTA (Network Traffic Analysis).
- Security data & workflow coordination solutions: SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation and Response).
By unifying these diverse security components, XDR empowers security teams to overcome siloed data and fragmented workflows, leading to a more structured security posture
XDR to bridge the security visibility gap
Extended detection and response (XDR) emerges as an open cybersecurity architecture (OCA) solution to address the challenges of siloed security tools. XDR offers a unified approach to security operations by integrating various tools and spanning across all application layer attacks (Figure 6).
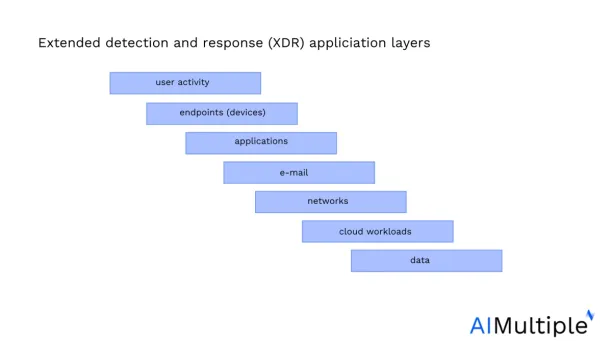
XDR’s Advantages
Enhanced visibility: Offers broader visibility across the entire security landscape, unifying data from various security tools.
Advanced detection: Leverages advanced analytics to identify complex threats and evade techniques used to bypass traditional SIEM solutions.
Improved response: Facilitates more effective correlation, investigation, and response to security incidents due to its unified approach.
What is UEBA in cybersecurity?
User Entity Behavior Analytics (UEBA) represents a new category of security solutions that leverage machine learning and deep learning for advanced threat detection.
UEBA focuses on understanding typical user and entity behavior within a network, enabling the identification of anomalies that might indicate potential security risks. This allows for earlier intervention and mitigation of potential security incidents.
Beyond Static Rules
Conventional security tools rely on predefined correlation rules and known attack patterns. These methods struggle to identify novel threats that deviate from established patterns.
- UEBA’s Advantage: offers a proactive approach by continuously learning user and entity behavior patterns. This allows it to detect anomalies that might signal:
- Compromised accounts
- Insider threats
- Zero-day attacks (previously unknown attacks)
While user behavior analysis is a core component, UEBA’s reach extends beyond just users. It can monitor a broader range of entities on a corporate network, including:
- Routers
- Servers
- Enterprise applications
- Internet of Things (IoT) devices
Benefits of Application Security Management (ASM)
Application security management (ASM) offers a range of advantages that strengthen an organization’s overall security posture. Here are some key benefits:
- Real-Time threat detection: continuously monitor applications for suspicious activity, enabling the identification and mitigation of threats in real-time. This reduces the window of opportunity for attackers and minimizes potential damage.
- Reduced analyst workload: by correlating data from various threat hunting and monitoring tools, ASM automates alert generation and prioritization. This frees up security analysts’ time from sifting through numerous notifications, allowing them to focus on more complex investigations.
- Customizable security controls: allows for the creation of rules and security event correlations based on an organization’s specific security posture and compliance requirements. This enables tailored protection against the most relevant threats.
- Machine learning integration: leverages algorithms to analyze historical data and identify patterns indicative of malicious activity. This proactive approach helps predict and prevent potential attacks.
- Log data management: centralizes and stores log data from various sources over extended periods. This facilitates efficient forensic analysis, allowing security teams to investigate historical incidents and identify root causes. Additionally, centralized log data simplifies compliance reporting by providing readily available audit trails.
To discover more on application security and compliance:
External Links
- 1. “https://www.statista.com/topics/11610/data-breaches-worldwide/”Retrieved on March 28, 2024.
- 2. “https://www.ibm.com/reports/data-breach”Retrieved on March 28, 2024.
- 3. “https://www.iso.org/standard/27001”Retrieved on March 28, 2024.
- 4. “https://www.iso.org/standard/65694.html”Retrieved on March 28, 2024.
- 5. “https://www.gartner.com/reviews/market/security-information-event-management”Retrieved on March 28, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.