Endpoint Security Stats in 24′ Based On Market & Incident Data
Endpoint security solutions, also called endpoint protection software, strengthen security measurements against cyber threats that result from cyber attacks, human errors, and endpoint management deficiencies. Even if no security vulnerabilities result in data breaches, companies are legally required to ensure the security of their sensitive data and fix vulnerabilities.
Collected and categorized data related to endpoint security, such as cyberthreats and incidents, is useful in understanding both its current and future state. This article presents endpoint security statistics, which cover market size, market players, incident reports, improving and depreciating factors.
Current statistics on endpoint security
Below are 5 categories that help us understand the effects of factors that play a role in endpoint security statistics.
1. Market size
There are multiple factors that affect endpoint security statistics, and improvements in technology are the frontrunners. Related to advancements in technology, businesses take advantage of improved technologies and turn to light-cost and easy-to-manage systems such as the cloud. In addition to improvements in technology, incidents such as the COVID-19 pandemic are capable of accelerating general trends around the world, such as remote working and BYOD.
Following changing factors, cyber attacks evolve and become more complex. Businesses, in return, opt for advanced endpoint security solutions. The following provides information on the global endpoint security market revenue and per-employee spend numbers.
Figure 1. Endpoint security worldwide revenue numbers between the years 2016 and 2028
The projected revenue by 2024 is $13.7 billion and $23.8 billion by 2028.

Source: Statista.1
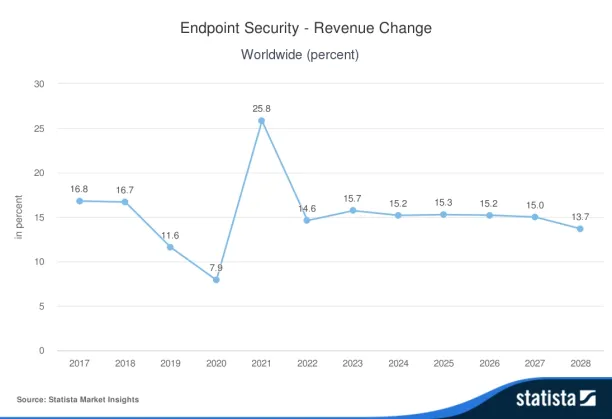
Figure 2. Endpoint security revenue change between the years 2016 and 2028
The highest revenue change, with nearly 25%, occurred in 2021 and correlates with the aftereffects of the COVID-19 pandemic, which was declared to be a worldwide pandemic at the beginning of March 2021 by the World Health Organization.
Source: Statista.2
Figure 3. Endpoint security global revenue comparison by 2025
The highest level of revenue is expected to come from the United States, with $6 million in 2025.
Source: Statista.3
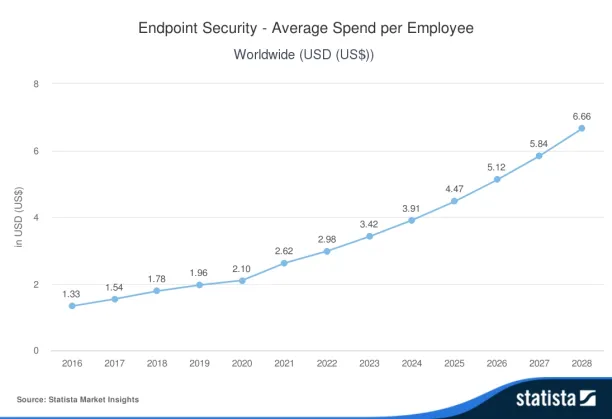
Figure 4. Average endpoint security spend per employee between the years 2016 and 2028
The average endpoint security spend per employee is expected to increase to $6.66 by 2028.
Source: Statista.4
2. Number of endpoints
Endpoints, by definition, are virtual and physical devices with endpoints that are able to transfer data. Endpoint examples are storage devices such as USBs, HDDs, SD cards, and IoT devices. Internet of Things devices are under the category of endpoints and cover any device that is able to communicate and connect to a network, including mobile devices, tablets, smart phones, and more.
Figure 5. Number of Internet of Things (IoT) connected devices worldwide from 2019 to 2030
It is projected that the number of IoT-connected devices will reach more than 29 billion in 2030.
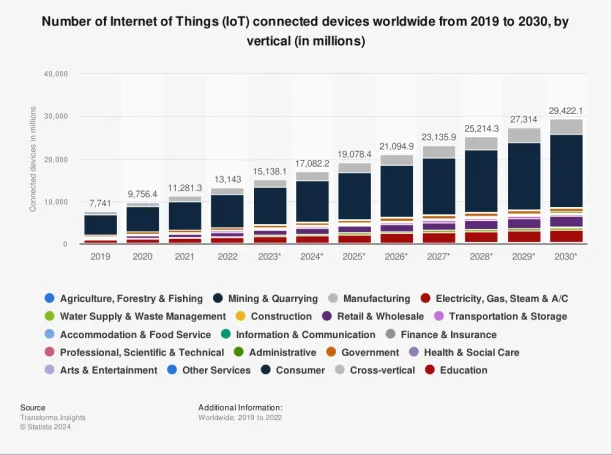
Source: Statista.5
3. Market players
Endpoint protection platforms (EPP) are a component of endpoint security solutions that aid in the first line of defense against malware. User reviews and market research platforms, G2 and Gartner, have illustrated the EPP market players below. For more on the comparative vendor table based on user reviews and ratings: Top 10 Endpoint protection software
Figure 6. Magic Quadrant* for Endpoint Protection Platforms
The figure below arranges market participants for endpoint protection platforms (EPPs) based on factors that are defined both above and below the sides.
*Magic Quadrant is a line of Gartner reports centered on the IT industry.

Source: Crowdstrike.6
Figure 7. G2 Grid® for Endpoint Protection Suites
The figure below arranges market participants for endpoint protection platforms (EPPs) based on factors that are defined at the corners.
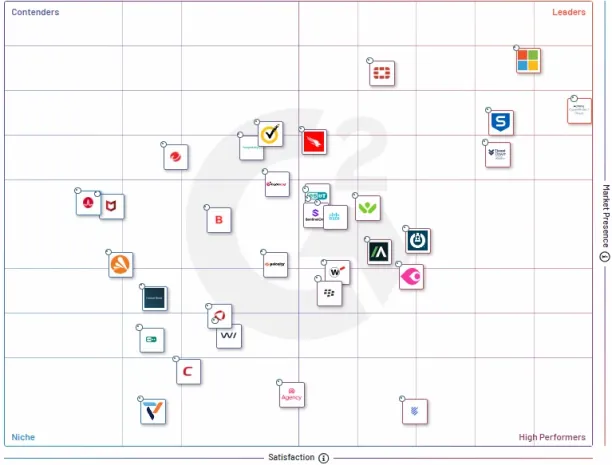
Source: G2.7
4. Factors that improve endpoint security
Below are listed factors backed by data that help utilize endpoint security better:
1. Organizational structure
The number of CISOs employed by Fortune 500 companies increased by 70% from 2018 to 2023. In contrast to Fortune 500 companies, small-sized businesses seem to disregard the need for CISOs and do not employ one.8
By aligning information security in their business, companies are 8 times more efficient at managing risks related to their business.9
2. Improving the human factor
The human factor still inexorably affects a business’s security status. According to the latest report, the human element is discernible in 74% of all data breaches, which consists of social engineering attacks, privilege misuse, miscellaneous use, error, and use of stolen credentials. 10
One effective way to reduce the human element is by teaching staff members about cyber security and threats.
For more on endpoint security best practices
5. Incident reports
For more on incident reports and endpoint security risks
FAQ
1. What is the difference between endpoint protection platform (EPP) and endpoint detection and response (EDR)?
Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR) are both crucial components of cybersecurity strategies aimed at protecting endpoints (individual devices like laptops, desktops, servers, etc.) within a network. While they both deal with endpoint security, they have distinct focuses and functionalities.
EPP primarily focuses on preventing cyber threats from infiltrating endpoint devices. It includes features such as antivirus, anti-malware, firewall, email filtering, web browsing protection, and other proactive measures to block known threats. EPP solutions often use signature-based detection (identifying known threats based on predefined patterns) and heuristic analysis (detecting suspicious behavior based on predefined rules) to prevent malware and other malicious activities.
EDR is more focused on detecting and responding to cyber threats that have already breached endpoint devices. It provides advanced threat detection capabilities by continuously monitoring endpoint activities, analyzing behaviors, and identifying suspicious or malicious activities.
Unlike EPP, which mainly relies on signature-based detection, EDR leverages techniques such as machine learning, behavioral analysis, and threat intelligence to detect unknown and sophisticated threats, including zero-day attacks. For more on endpoint security
2. What is the difference between intrusion detection and response (IDR) and EDR?
Intrusion Detection and Response (IDR) and Endpoint Detection and Response (EDR) are both crucial components of cybersecurity strategies aimed at detecting and responding to security incidents. While they share similarities, they operate at different levels within a network and have distinct focuses and functionalities.
IDR is a broader concept that encompasses detection and response mechanisms deployed across an entire network infrastructure, including endpoints, servers, network devices, and other critical assets, while EDR, as discussed earlier, specifically focuses on detecting and responding to security threats at the endpoint level, such as individual devices like desktops, laptops, servers, and other endpoints connected to the network.
Further reading
- Top 10 Hexnode Alternatives Based on 10,800+ Reviews
- Top 10 RMM Software: Analysis From 7,700+ Reviews
- Top 10 Endpoint Management Software: 12K+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:
External resources
- 1. “Endpoint Security – Worldwide”. Statista. Accessed: 27/March/2024.
- 2. “Endpoint Security – Worldwide”. Statista. Accessed: 27/March/2024.
- 3. “Endpoint Security – Worldwide”. Statista. Accessed: 27/March/2024.
- 4. “Endpoint Security – Worldwide”. Statista. Accessed: 27/March/2024.
- 5. “Number of Internet of Things (IoT) connected devices worldwide from 2019 to 2030, by vertical.” Statista. Accessed: 27/March/2024.
- 6. “2023 Gartner® Magic Quadrant™ for Endpoint Protection Platforms”. Crowdstrike. Accessed: 27/March/2024.
- 7. “G2 Grid® for Endpoint Protection Suites”. G2. Accessed: 28/March/2024.
- 8. “What Is A Chief Information Security Officer? CISO Explained”. Forbes. Accessed: 28/March/2024.
- 9. Mishra, Ashish (2023). “Modern Cybersecurity Strategies for Enterprises”. London: BPB Online. p. 80.
- 10. “2023 Data Breach Investigations Report”. Verizon. Accessed: 21/March/2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.