15+ Components of a Detailed Firewall Audit Checklist in 2024
Firewall audits are critical for maintaining network security and ensuring compliance with industry standards and regulatory requirements. Firewall audit software plays a crucial role by offering automated tools to scrutinize and manage firewall rules, configurations, and the overall security posture.
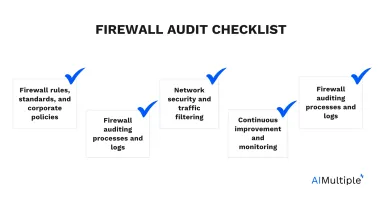
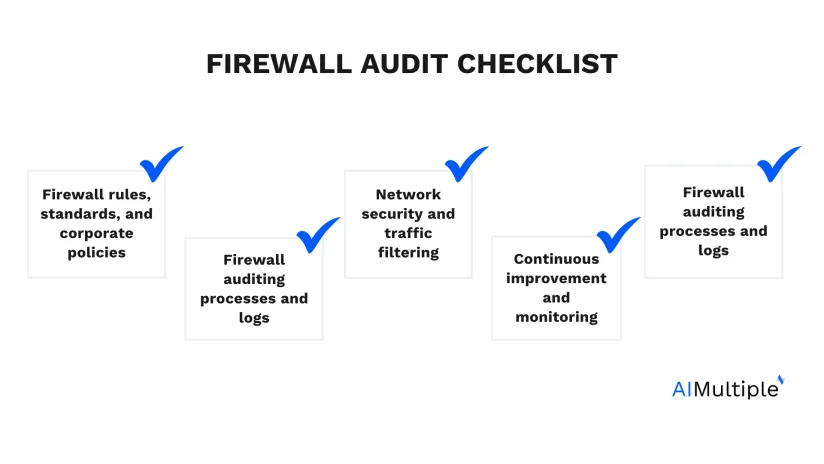
The five main points in the firewall audit checklist are examining firewall rules, standards, and compliance with corporate security policy; keeping track of the history of firewall audit processes and logs; examining network security and traffic filtering; maintaining continuous improvement and monitoring; and creating awareness about firewall compliance.
This comprehensive article outlines a firewall audit checklist for conducting thorough firewall audits, optimizing firewall configurations, and enhancing overall network security posture.
Firewall rules, standards, and corporate policies
1. Firewall rule base
Begin by reviewing the firewall rule base, ensuring that it aligns with corporate security policies and relevant industry standards.
Identify redundant rules and overly permissive configurations to minimize security risks.
2. Firewall standards
Ensure that firewall configurations comply with relevant industry standards and regulatory requirements, such as PCI DSS, HIPAA, and GDPR.
Implement security controls and measures to protect sensitive data and ensure regulatory compliance.
3. Corporate security policy
Assess the firewall configuration to ensure it follows secure practices and adheres to corporate security policies.
Enforce object naming conventions and disable unnecessary services to enhance security.
4. Optimizing firewall rules
Optimize firewall rules to reduce complexity and improve performance.
Eliminate redundant rules and error-prone manual tasks to streamline rule management processes.
5. Location-based firewall configurations
Differentiate rule sets for internet-facing and internal network firewalls.
Firewall auditing processes and logs
6. Firewall audit process
Establish a formal and controlled process for conducting firewall audits regularly.
Ensure that audit procedures are comprehensive and cover all critical aspects of firewall configuration and security.
7. Firewall logs
Regularly review firewall logs to detect security incidents, unauthorized access attempts, and anomalies in network traffic.
Maintain accurate audit logs to facilitate forensic analysis and compliance reporting.
8. Complete audit trail
Maintain a complete audit trail of firewall management activities, including rule changes, access requests, and security incidents. This ensures accountability and provides evidence for compliance audits.
Network security and traffic filtering
9. Risk Assessment
Conduct a comprehensive risk assessment to identify vulnerabilities and security gaps in firewall configurations.
Prioritize remediation efforts based on the severity of identified risks.
10. Access control
Enforce secure configurations for firewalls to minimize security risks and protect against unauthorized access.
Implement access controls and restrict overly permissive rules to prevent potential security breaches.
Implement packet filtering for DNS traffic to prevent unauthorized zone transfers and ensure only authorized responses are allowed.
Specify rules to allow traffic originating only from internal networks and log any traffic from external sources to enhance network segmentation and access control.
11. Remote access
Enforce the use of secure protocols like secure shell (SSH) instead of Telnet to prevent unauthorized access if remote access is required.
Segment fire transfer protocol (FTP) servers in separate subnets to protect internal networks.
Continuous improvement and monitoring
12. Backup and recovery plan
Develop a comprehensive backup and recovery plan for firewall configurations to ensure continuity of operations in case of failures or security incidents.
Regularly test backups to verify their integrity and reliability.
13. Patches, updates, and compliance
Test and install the latest patches and updates for firewall products to address vulnerabilities and enhance security.
Verify that updated firewall rule sets comply with organizational security policies, rules, and industry standards like PCI DSS, GDPR, and relevant firewall vendor information.
14. Change management processes
Implement robust change management processes to track and manage firewall changes effectively.
Ensure that changes are documented, tested, and approved before implementation to minimize the risk of errors and vulnerabilities.
15. Continued availability and disaster recovery
Maintain hot standby systems for primary firewalls to ensure continued availability and disaster recovery capabilities.
Implement backup and recovery plans for firewall configurations, and rule sets to minimize downtime in case of security incidents.
Training and awareness
16. Administrator training
Provide in-depth training for firewall administrators on firewall configuration, rule management, and monitoring.
Ensure administrators are familiar with firewall audit processes, compliance requirements, and security standards relevant to the organization.
Train administrators on incident response procedures, including how to handle security breaches, perform forensic analysis, and implement remediation measures.
17. User training
Conduct regular training sessions for users to educate them about firewall security, best practices, and security policies.
Provide guidance on identifying and reporting suspicious activities or potential security incidents to the IT security team.
Train users on safe browsing habits, recognizing phishing attempts, and avoiding risky online behavior that could compromise network security.
FAQs
How does a firewall audit work?
A firewall audit is a multifaceted procedure that provides organizations with visibility into the status and efficacy of their network-wide firewall deployments. Prior to implementation, every new rule requires thorough analysis and simulation. Additionally, a comprehensive and precise audit log must be consistently maintained for each change made.
How often should firewalls be audited?
As a general rule, it is recommended to review and update firewall rules and policies annually or more frequently if operating in a dynamic or high-risk environment. However, it’s crucial to regularly reassess firewall rules to ensure they remain effective and pertinent to your security needs.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.