Top 4 Microsoft System Center Alternatives in 2024
Network security statistics show that data breaches exposed over 6 million data records globally during the first quarter of 2023.
Companies that deal with complex security rules and firewall assessment methods, each with different requirements, may find it difficult to manage network security policies that will prevent the IT environment from data breaches.
Digital-first organizations can use network security policy management (NSPM) solutions (NSPM) to set, analyze, and implement security policy designs across their organization’s network.
However, NSPM solutions can be difficult to evaluate. This article discusses the top 4 Microsoft System Center Alternatives for network security policy management, providing a side-by-side comparison of their features and market presence based on user reviews to show each vendor’s specifications.
Top 4 Microsoft System Center Alternatives
Table 1: Feature comparison of top 4 Microsoft System Center alternatives
| Vendors | Integrations | Pricing driver | Operation systems | Deployment options |
|---|---|---|---|---|
| Microsoft System Center | N/A | N/A | N/A | Hyper-V VMware Physical servers |
| AlgoSec | AWS, Cisco, Microsoft Azure, VMware, GCP | N/A | CentOS 7 | Physical appliances Virtual appliances Cloud-based solutions |
| SolarWinds Network Configuration Manager | Cisco,
Cisco ASA,
Cisco Nexus,
Dell, Adtran,
Arris,
Aruba,
Nortel,
Nortel Alteon,
Nortel BayStack,
Extreme,
Marconi,
Radware,
Netscreen,
Motorola,
HP,
Netscalar,
Juniper,
Foundry,
F5
| Number of endpoints | Windows Windows Server 2022 Base windows-server-2022-english-full-base-x86/x.x.x | Physical appliances Virtual appliances |
| Tufin | AWS,
GCP,
Microsoft Azure,
Red Hat,
Check Point,
Cisco, Cisco ACI,
F5 Networks ,
Fortinet,
Forcepoint ,
Netfilter/IPtables,
Juniper Networks,
OpenStack,
Palo Alto
Networks,
dSymantec
| Usage | TufinOS Red Hat Enterprise Linux (RHEL) 7 CentOS 7 | Physical appliances Virtual appliances Cloud-based solutions |
| Trend Micro TippingPoint | N/A | N/A | Linux/Unix | On-premises Virtual environments |
*AWS Firewall Manager is not tied to any particular operating system in the way traditional applications are. It serves as a centralized platform for managing firewall rules across various AWS accounts.
Core features: Each vendor listed in the provided table offers compatibility with the specified features:
- Automated security policy management: Streamlines the process of securing networks by reducing manual overhead in managing complex network environments.
- Workload monitoring: Monitors the application, the data it generates, and the network resources supporting user-application interactions.
- Endpoint protection: Safeguarding endpoints, devices like laptops, smartphones, and tablets, enabling threat hunting and automated response actions.
- Support for hybrid environments: Maintaining a consistent security policy platform across all environments to streamline security operations.
- Integration with cloud platforms: Understanding and addressing the security challenges presented by cloud environments.
Table 2: The market presence of the top 4 Microsoft System Center alternatives
| Vendors | Total reviews** | Average rating** (5-point scale) |
|---|---|---|
| Microsoft System Center | 762 | 4.1 |
| AlgoSec | 393 | 4.4 |
| SolarWinds Network Configuration Manager | 375 | 4.4 |
| Tufin | 296 | 4.0 |
| Trend Micro TippingPoint | 188 | 4.1 |
**Based on the total number of reviews and average ratings on Gartner, G2, PeerSpot, and TrustRadius software review platforms as of 01/09/2024.
Disclaimer: Vendors are sorted by the total number of reviews in descending order.
Vendor selection criteria: Given the abundance of NSPM software available, the list (above) has been narrowed down using the vendor criteria listed below.
- Number of reviews: 100+ reviews on Gartner, G2, PeerSpot, and TrustRadius.
- Average rating: 4.0/5 and above on Gartner, G2, PeerSpot, and TrustRadius.
Different types of network security policy management (NSPM) features
NSPM software offers various network security features:
- Network security policy management
- Intrusion prevention
- Firewall audit
- Zero trust access
- VPN
- Cloud network security
- Role-based-access control (RBAC)
- Mandatory access control (MAC)
Microsoft System Center
Microsoft System Center is an IT management solution with network security policy management, network monitoring, software updates, and patches, and endpoint security (including anti-malware) capabilities.
The product is available in two plans: standard and datacenter. The datacenter plan includes data virtualization for high-density private clouds, and the standard plan is for partially or non-virtualized private cloud workloads.
Pros
Ease-of-use and deployment: Some users say that the product provides efficient administration of resources, and easily automates application development for both private and public cloud usage.1
Reporting: Some customers claim that Microsoft System Center can successfully create KPIs and management reports with monthly presentations on activities.2
Integrations: Some users conclude that more software integrations can be provided (e.g. Intune Configuration Manager interaction).3
Cons
Learning curve: Some customers highlight that the learning process might be challenging for beginners.4
Price: A few customers find the solution expensive compared to the services it offers.56
Knowledge-base: Some users note that there is a need for more extensive documentation and wiki pages.7
Top 4 Microsoft System Center Alternatives
1- AlgoSec
AlgoSec is a network security policy management (NSPM) platform that assists companies in implementing network security policies and enabling application connection across their network (on-premises, cloud, or hybrid).
AlgoSec improves network visibility by leveraging its network traffic monitoring capabilities, combining firewall rules into business applications, and detecting compliance issues.
Pros
Firewall assessment: Reviewers appreciate how AlgoSec can analyze firewall configurations and recommend methods to organize them.8
Deployment and integrations: Customers denote that the ease of deployment and easy integration of firewalls make cloud administration effortless.9
Rule implementation: Senior specialists express that the rule implementation is simple, and the end-to-end workflow may be easily monitored using AlgoSec.10
Cons
Customer support: Some users indicate that customer support might be slow and too broad without details due to a lack of available documentation.11
Reports: Security administrators claim that the reports are lacking information. They don’t receive URL or application data from other software such as Cisco FTDs.12
Patching: Some users report that the patching in AlgoSec is not working properly.13
2- SolarWinds Network Configuration Manager
SolarWinds Network Configuration Manager, based on the SolarWinds Platform, is a solution that helps users manage and automate network configuration management. NCM improves availability, saves time, enhances security, and assures policy compliance. NCM has automation tools that minimize the time network engineers spend on routine network operations, allowing them to concentrate on mission-critical network initiatives.
SolarWinds Network Configuration Manager integrates routers, switches, firewalls, load balancers, and wireless access points into a centralized console.
Pros
Automation: IT specialists state that automation capabilities have had a significant influence on workflows, allowing actions like configuration backups, template deployment, and firmware updates to be automated.14
Compliance reporting: Some users denote that compliance reporting capabilities give detailed insights into network compliance, including pre-built network audit reports.15
Cons
Network visibility: IT professionals note that network insights may be improved.16
Network mapping: Some users suggest that improvements are required in the automated network mapping function.17
Customization: Some reviewers convey that customization isn’t as straightforward, it may be made simpler.18
3- Tufin
Tufin offers network security solutions for companies with up to 10,000+ IoT devices and 200M+ routes to control, run, and monitor networks that contain many routers, switches, firewalls, and other network devices by leveraging its network security policy management, network security policy management, and network automation technologies.19
Key features of Tufin include the following:
- Automated network security policy management: Controls network endpoints on internal networks and in the cloud, enabling security teams to provide network access.
- Firewall assessment: Enables businesses to maintain, control, and modify firewall rules for on-premises and cloud firewalls.
Read more: Firewall audit, top 12 firewall audit software, Next-generation firewalls: NGFW features. - Network segmentation: Uses microsegmentation, OT network segmentation, and/or fully automated zero trust network access (ZTNA).
- Network audit: Maintains control over AI audit efforts while ensuring regulatory compliance.
- Vulnerability-based change automation (VCA): Integrates with vulnerability scanners and vulnerability testing tools, and continuously scans for vulnerabilities before implementing new cybersecurity policies.
- Network traffic monitoring: Analyzes network traffic and enhances network visibility to identify potential problems, security threats (e.g. insider threats), and performance bottlenecks.
Figure 1: Tufin’s products and services
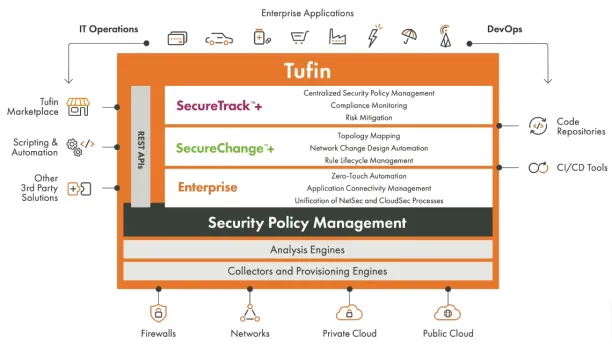
Source: Tufin20
Pros
Customization: Some customers express that Tufin provides a high-level of customizability (e.g. when limiting user access or creating workflows).21
Read more: Role-based-access control (RBAC), mandatory access control (MAC).
Zone-based policy permissions: Users appreciate the fact that Tufin allows them to define a zone-based policy in which they can decide what to auto-permit and what to block in the queue before pushing the changes to firewalls.22
Read more: Demilitarized zone (DMZ) security.
Security network auditing: Some customers note that Tufin’s security auditing capability can effectively evaluate the company’s policies and compliance, and also create rules across multiple gateways and firewalls effectively.23
Cons
Microsegmentation integration with Cisco ACI: Some users who indicate that they need to deploy micro-segmentation to their system are having an issue with Tufin, which does not presently enable integration with Cisco ACI for micro-segmentation.24
Read more: Top 10 microsegmentation tools.
Hardware requirements: Some users expect to see the hardware requirements to be lowered, stating that to operate the solution, the hardware platform is required to meet high criteria. These high standards are challenging to meet for users.25
Security policy rule customization: Some users argue that Tufin might improve its rule customization processes.26
Read more: Most popular Tufin competitors: AlgoSec alternatives and Firemon alternatives.
4- Trend Micro TippingPoint
Trend Micro TippingPoint is a network security platform with intrusion prevention capabilities that helps to mitigate advanced threats like malware and phishing against both known and undetected vulnerabilities.
Trend Micro TippingPoint identifies and stops network assaults by integrating firewall technologies including deep packet inspection, threat reputation, URL reputation, and malware detection.
Read more: Firewall risk assessment (firewall types), next-generation firewall: NGFW features.
Pros
Intrusion prevention system (IPS): According to user reports, Tipping Point’s network intrusion prevention system (IPS) effectively streamlines user operations, offering a consolidated point of control for managing third-party risks.27
Stability: Some reviewers note that with Trend Micro TippingPoint the network is reliable, with zero latency.28
Low-code / no-code: Users appreciate the fact that the product includes both intrusion prevention system (IPS) and intrusion detection system (IDS) configurations on the graphical user interface (GUI); there is no need to use the command line interface CLI to input commands.29
Cons
Performance: Some reviews reveal that the product’s performance is poor, and the focus on application resiliency can be improved.30
User interface: Some users suggest that Trend Micro TippingPoint Threat Protection System user interface can be improved.31
Bandwidth capacity: Some users say that Trend Micro TippingPoint Threat Protection System does not have adequate capacity to manage necessary traffic.32
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External links
- 1. ”Microsoft System Center Reviews“. G2. July 24, 2022. Retrieved March 28, 2024.
- 2. ”Microsoft System Center Reviews“. PeerSpot. March 13, 2023. Retrieved March 28, 2024.
- 3. ”Microsoft System Center Reviews“. PeerSpot. March 13, 2023. Retrieved March 28, 2024.
- 4. ”Microsoft System Center Reviews“. TrustRadius. June 2, 2022. Retrieved March 28, 2024.
- 5. ”Microsoft System Center Reviews“. G2. July 24, 2022. Retrieved March 28, 2024.
- 6. ”Microsoft System Center Reviews“. TrustRadius. June 2, 2022. Retrieved March 28, 2024.
- 7. ”Microsoft System Center Reviews“. TrustRadius. June 2, 2022. Retrieved March 28, 2024.
- 8. ”AlgoSec Reviews“. G2. February 27, 2024. Retrieved March 28, 2024.
- 9. ”AlgoSec Reviews“. G2. February 27, 2024. Retrieved March 28, 2024.
- 10. ”AlgoSec Reviews“. G2. February 27, 2024. Retrieved March 28, 2024.
- 11. ”AlgoSec Reviews“. Gartner. November 1, 2023. Retrieved March 28, 2024.
- 12. ”AlgoSec Reviews“. PeerSpot. June 29, 2021. Retrieved March 28, 2024.
- 13. ”AlgoSec Reviews“. TrustRadius. November 3, 2023. Retrieved March 28, 2024.
- 14. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. March 27, 2024. Retrieved March 28, 2024.
- 15. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. March 27, 2024. Retrieved March 28, 2024.
- 16. ”SolarWinds Network Configuration Manager Reviews“. TrustRadius. November 16, 2023. Retrieved March 28, 2024.
- 17. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. February 28, 2024. Retrieved March 28, 2024.
- 18. ”SolarWinds Network Configuration Manager Reviews“. TrustRadius. March 12, 2023. Retrieved March 28, 2024.
- 19. ”Network Security Policy Management“. Tufin. Retrieved March 28, 2023.
- 20. ”Network security orchestration“. Tufin. January 2024. Retrieved March 28, 2023.
- 21. ”Tufin Reviews“. G2. November 20, 2023. Retrieved March 28, 2024.
- 22. ”Tufin Reviews“. G2. November 20, 2023. Retrieved March 28, 2024.
- 23. ”Tufin Reviews“. PeerSpot. January 26, 2023. Retrieved March 28, 2024.
- 24. ”Tufin Reviews“. PeerSpot. August 29, 2021. Retrieved March 28, 2024.
- 25. ”Tufin Reviews“. PeerSpot. October 7, 2022. Retrieved March 28, 2024.
- 26. ”Tufin Reviews“. PeerSpot. August 29, 2021. Retrieved March 28, 2024.
- 27. ”Trend Micro TippingPoint Reviews“. PeerSpot. August 28, 2023. Retrieved March 28, 2024.
- 28. ”Trend Micro TippingPoint Reviews“. G2. August 14, 2023. Retrieved March 28, 2024.
- 29. ”Trend Micro TippingPoint Reviews“. G2. December 14, 2023. Retrieved March 28, 2024.
- 30. ”Trend Micro TippingPoint Reviews“. G2. July 01, 2023. Retrieved March 28, 2024.
- 31. ”Trend Micro TippingPoint Reviews“. PeerSpot. January 1, 2023, 2023. Retrieved March 28, 2024.
- 32. ”Trend Micro TippingPoint Reviews“. PeerSpot. September 13, 2023, 2023. Retrieved March 28, 2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.