Most Common Cyber Attack Vectors in 2024 & How to Prevent Them
The cyber attack disruption levels have surged by 200% from 2019 to 2024, compared to a 4% increase from 2011 to 2016.1
The rise of cyber attacks is alarming since damage to information systems can harm processes, assets, individuals, and organizations by exploiting vulnerabilities that violate information security.
Understanding the attack methods is critical for leveraging effective cybersecurity practices such as intrusion prevention or network security policy management against cybersecurity risks. Thus, this article covers cyber attack vectors (e.g. their effects, and types) and methods for organizations to prevent, detect, and respond to these attack vectors.
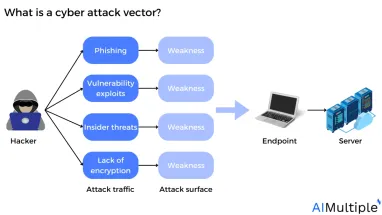
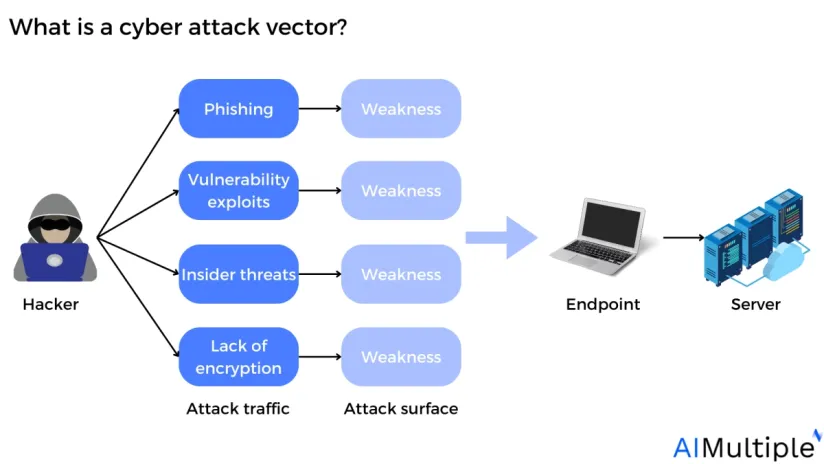
What is a cyber attack vector?
A cyber attack vector is any systematic attempt to access, expose, malfunction, or disrupt software, information, or other assets via unauthorized entry to a system, or IoT device.
Example: Assume a security guard is charged with protecting valuable items in a department store. An intruder might access and escape the store by various doors, including the front door, back door, or stairs. An intruder might also enter the store by another means, for example by imitating a store employee. All of these approaches constitute attack vectors, which the security guard may attempt to block by monitoring and controlling all doorways and checking employees to see their identities.
Similarly, all computer networks have vulnerable spots where attackers might get access. Because current computer systems and software settings are complicated, blocking all attack routes is usually impossible. However, network security policy management (NSPM) solutions or intrusion detection and prevention (IDPS) tools can block the majority of attack routes, thus making it far more difficult for attackers to exploit them.
What are the common types of cyber attack vectors?
Cybercriminals implement a variety of advanced tools and strategies to launch attack vectors on organizations’ computer networks, operational technology, and other targets.
Some of the most popular forms of cyberattacks are:
1. Malware
Malware is malicious software that may make infected computers impractical. Malware can alter data, steal information, and even delete files that are required for the operating system (OS) to function properly.
Figure 1: Annual number of malware attacks in selected countries in 2022 (in millions)
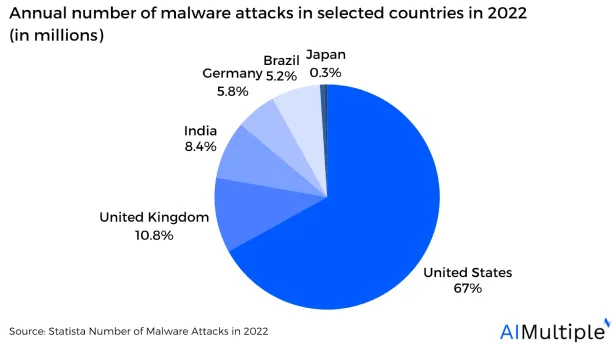
Source: Statista2
Malware takes numerous forms, including:
- Trojan horses pose themselves as beneficial applications or hide within legitimate software to mislead individuals into downloading them. A Trojan works by developing a hidden entry point on the targeted device and installing further malware once it has gained access.
- Ransomware is a type of malware that encrypts files on a device, making any files or programs that rely on them useless. Ransomware is the second most common type of cyberattack, accounting for 17% of attacks.3
Figure 2: How crypto-ransomware works
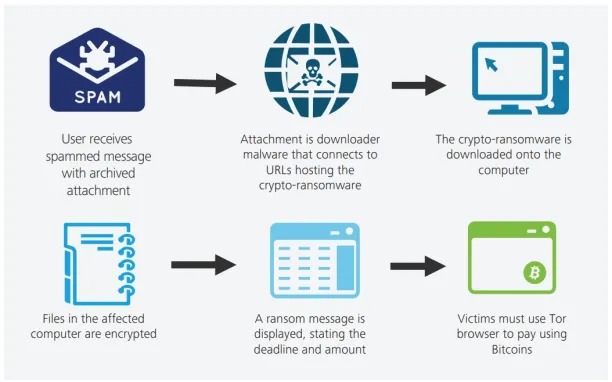
Source: Deloitte4
- Scareware is a hacking method that manipulates people into visiting faked or virus-ridden websites or installing harmful software (malware). Scareware can take the shape of pop-up advertising that shows on a user’s computer or is propagated by spam email assaults.
A scareware assault is frequently conducted via pop-ups that appear on a user’s screen, informing them that their machine or files have been infected and providing solutions. This social engineering strategy attempts to scare individuals into purchasing software that claims to give an instant solution to the “problem.” However, rather than resolving a problem, scareware contains malware designed to steal the user’s personal information from their device.
- Spyware is malicious software that collects information about an individual or organization and sends it to another entity in a way that impacts the user by violating their data, risking the privacy and security of their device.
- Worms are malware software that replicates quickly and spreads over a network. As it spreads, a worm absorbs bandwidth, overwhelming infected computers and rendering them inefficient or unavailable. Worms may also modify and remove data, and introduce new viruses.
2. Social engineering
Social engineering refers to a collection of strategies intended to manipulate, persuade, or deceive a victim into disclosing sensitive information or doing ill-advised actions to reveal financial and personal data or gain control of a computer system.
Some typical instances of social engineering methods are:
- Phishing attacks utilize emails or SMS messages to get user passwords, steal private information, or transmit malware. Phishing emails are frequently crafted to appear real. They normally persuade the victim to click a link that leads to a malicious site or download a file that contains malware. Phishing is the second most prevalent source of breaches.5 Cybercriminals have also evolved into increasingly complex means of phishing:
Spear phishing attacks attempt to deceive a single individual, frequently by leveraging information from the victim’s accessible social media accounts to make the scam appear to be more credible.
Whale phishing attacks are a spear phishing method that focuses on high-level business leaders.
- Business email compromise (BEC) attacks attempt to mislead the target into completing a business function for a fraudulent purpose, like sending money. The attacker aims to pretend to an executive to be persuasive or to generate a feeling of obligation in the targeted employee.
- Baiting occurs when hackers persuade people to provide personal data or allow malware to be installed on their computers by offering them false promises.
Baiting scams can take the shape of enticing web-based advertisements offering free downloading or upgrades. The attacker expects that the password the target enters to accept the offer is one they have previously used on other websites. Thus, the attacker can access the target’s passwords.
Read more: Phishing vs whaling.
3. Denial-of-service attacks
A denial-of-service (DoS) attack happens when a malicious threat actor prevents authorized users from accessing information systems (e.g. devices).
To block access for authorized users, a denial-of-service condition is achieved by overloading the targeted network with traffic until it either crashes or becomes inaccessible.6
The most popular DoS attack technique involves flooding a network host with traffic:
- A smurf attack involves the attacker impersonating the target machine and using its fake source IP address to send internet messages to several hosts. The targeted host will subsequently get an inflow of responses from the recipients of these packets.
- A SYN flood (half-open attack) happens when an attacker tries to gain access to the target server by sending a request but fails to finish the connection through the Transmission Control Protocol (TCP)/IP network that establishes a link between a local host and server. The connected port is left in an occupied state and is not available for new requests due to the unfinished connection. All open ports will be flooded with requests from an attacker, making it impossible for authorized users to connect.
4. Man-in-the-middle attacks
A man-in-the-middle (MITM) attack, also known as an in-path attack, is a type of cyberattack that occurs when an attacker secretly sends communications between two parties that assume they are speaking with each other directly.
MITM attacks are frequently conducted using unencrypted public wifi networks, where attackers can easily intercept traffic.
5. Other types of cyber attack vectors
- Structured query language (SQL) injection is a method that aims to manipulate the connection between a webpage and the database that supports it. Usually, the goal is to induce malicious code to run on the database’s server. Access controls, untyped user input, or database vulnerabilities are frequently combined to create SQL injection attacks.7
- Fileless malware (in-memory malware) is an attack vector that doesn’t require traditional file storage because it lives only in a computer’s memory (e.g. RAM).
- Domain name system (DNS) spoofing, also known as DNS cache poisoning, is a type of cyber attack vector where malicious data is injected into the DNS cache, resulting in the name server returning a false result record, such as an Internet Protocol (IP) address. Thus, traffic is subsequently redirected to the attacker’s preferred computer.
- Zero-day exploits are cyber attack vectors that focus on an undetected or unresolved security vulnerability in hardware or software. “Zero day” describes a software or hardware issue where malicious parties can immediately access it, giving the vendor zero days to repair it.
- Cross-site scripting (XSS) is an injection attack where a threat actor inserts malicious scripts or other data into material that is hosted on legitimate websites. After that, the content with malicious code is sent to the victim’s browser.
Cyber attack prevention, detection and response
Companies put threat management strategies into practice to prevent their most valuable resources and assets.
Cyber attack prevention methods
- Identity and access management (IAM) tools help administrators regulate user access to vital information within their companies by using IAM tools. Privileged access management, two-factor authentication, multi-factor authentication, and single sign-on systems are some of the technologies used in IAM tools.
- Data loss prevention (DLP) helps prevent unauthorized or risky sharing, transferring, or use of sensitive data. It can assist companies in keeping an eye on and securing private data across endpoints, cloud-based locations, and on-premises systems.
Read more: Top 10 data loss prevention or DLP software.
- Firewalls aim to block network traffic from threats gaining access to a device. Firewalls can filter traffic by modifying the source and destination IP addresses, IP protocols, and source and endpoint port codes.
Read more: Firewall assessment.
- Vulnerability prevention methods, such as patch management (the process of deploying firmware, operating system (OS), and application updates to devices), and periodic penetration testing, can help block vulnerabilities before attackers execute them.
Read more: Pentesting tools.
- Attack surface management (ASM) software can detect, list, and fix potentially unsecured assets before cyber attack vectors identify them.
- Unified endpoint management (UEM) technologies can apply security controls and guidelines to all endpoints on the business system.
Read more: Top 10 endpoint management software.
Cyber attack detection methods
It is challenging to prevent cyber attack attempts, thus businesses may also utilize early detection methods to identify cyber attack vectors.
- Security information and event management (SIEM) systems collect and track communication from various internal cybersecurity technologies (e.g. intrusion detection and prevention systems (IDPSs), endpoint detection and response systems (EDRs)).
- Cyber threat intelligence (CTI) platforms enhance security alerts to assist administrators in comprehending the types of threats they may encounter.
- Antivirus programs may scan machines for risky applications and automatically remove malware.
- Threat hunting techniques can detect stealthy threats (e.g. advanced persistent threats (APTs)).
Cyber attack response methods
- Data breach incident response strategies can assist limit and eliminating cyber attacks, maintaining damaged networks, and identifying the underlying causes to prevent further attacks.
- Security orchestration, automation, and response (SOAR) technologies can help administrators organize diverse security products into automated protocols for intrusion prevention in real-time.
- Extended detection and response (XDR) systems help automate complex cyberattack prevention, detection, and response processes such as threat hunting. XDR gathers and correlates data from email, endpoints, computers, cloud workloads, and networks, providing network visibility. Threats may then be examined, prioritized, tracked down, and resolved to avoid data loss and breaches.
3 motives behind cyber attack vectors
1. Criminal
Criminally motivated attacks seek financial benefit by stealing funds, and information, or disrupting business operations. Hackers can either break into a bank account to take funds directly or use social engineering scams to mislead individuals into transferring money to them. Hackers may steal personal information and use it to execute identity theft, trade it on the dark web, or keep it as a hostage.
2. Personal
Personally motivated criminals, such as upset current or past workers, seek revenge for a perceived injustice. They may steal assets, and confidential information, or destroy a company’s infrastructure.
3. Political
Politically motivated attackers are frequently associated with electronic warfare, and “hacktivism.” In cyber warfare, nations frequently attack their adversaries’ government agencies or key infrastructure. Activist hackers, known as “hacktivists,” may not damage their victims significantly. Instead, they try to draw attention to their causes by publicly exposing their attacks.
Negligent threats: While negligent users could harm their organizations, a cyber attack occurs when an individual purposefully utilizes their privileges to carry out threatening conduct. An employee who negligently keeps sensitive information on an insecure drive is not conducting a cyber attack; an upset employee who intentionally copies secret material for personal gain is.
Who is causing the cyber attacks?
Illegal groups, politicians, and private individuals can all launch cyber attacks. Criminals can be classified as either outsider or insider threats.
Outsider threats are not permitted to utilize a network or device but still break in. External cyber threat actors comprise organized crime associations, skilled hackers, government-backed individuals, and amateur hackers.
Insider threats are users with authorized and lawful authority over a company’s resources who purposefully or unintentionally abuse their rights. This group covers staff, vendors, customers, contractors, and subcontractors with system access.
Read more: Top 10 insider threat management software.
What are the targets of cyber attack vectors?
Threat actors usually breach IT systems because they’re seeking specific items.
Common targets of cyber attack vectors are:
- Business financial data
- Client data (may include personally identifiable data)
- Contact information and login credentials
- Intellectual property, (e.g. trade secrets and product ideas)
In some circumstances, cyber attackers are hesitant to acquire anything at all. Rather, they just seek to disrupt computer networks or IT infrastructure that negatively impact a business, authority, or another target.
5-stages of a cyber attack
Figure 3: 5-stages of a cyber attack
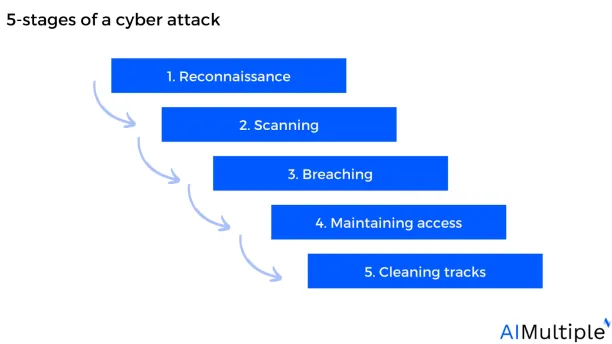
1. Reconnaissance
During the reconnaissance phase, attackers seek to gather precise information about the target employee or organization, including identifying key online actions.
The attacker can simply search for “system administrator” on social media sites like LinkedIn To obtain the employee names and roles (see below).
Figure 4: People results for system administrator

2. Scanning
Scanning entails using the information gathered during reconnaissance to investigate the network. Attackers search for any information that may assist them carry out the “breach,” including machine names, IP addresses, and login credentials.
During the scanning phase, the attackers also scan the target’s network for weaknesses. For example, the attacker may attempt to identify the target’s system specifications (e.g. whether it uses antivirus software).
3. Breaching
During the breaching phase, an attacker will achieve one or more of the following goals to breach the organization’s network:
1) Gaining unauthorized entry to one or more targeted databases.
2) Conducting application-level attacks against web-based services.
3) Launching denial-of-service attacks against services operating in the system under attack.
For instance, a malicious individual could spoof the e-mail address of the employee on vacation and then send the spoof e-mail to HR, claiming that he or she demands access to specific records but has forgotten their login credentials. If the HR submits the account and password without suspecting the fake email the attacker will obtain the necessary credentials to breach the network.
4. Maintaining access
Once an attacker has acquired access, they intend to maintain it to prevent further attacks. Attackers may protect the system against other hackers or security employees by using Trojans to ensure exclusive access. Once the attacker has taken control of the system, they might utilize it as a base of operation to launch more attacks.
5. Cleaning tracks
Covering tracks implies that the attacker should eliminate any evidence of detection. Attackers may hide their activities to evade discovery by security staff and continue to use the hacked system. Attackers may try to remove all signs of the attack, including data logs and intrusion detection alerts.
Overlapping between stages: There is an overlap between the five phases; for instance, an attacker who breached the organization’s network in stage 3 then can use that access to keep scanning in stage 2 and perform reconnaissance in stage 1.
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External links
- 1. ” Reinvention in the age of generative AI“. Accenture. January 12, 2024. Retrieved March 21, 2024.
- 2. ”Annual number of malware attacks in selected countries in 2022“. Statista. May 3, 2023. Retrieved March 21, 2024.
- 3. ”IBM X-Force Threat Intelligence Index 2024“. IBM. 2024. Retrieved March 21, 2024.
- 4. ”Ransomware Holding Your Data Hostage“. (PDF). Deloitte. August 12, 2016. Retrieved March 24, 2024.
- 5. ”Cost of a Data Breach Report 2023“. IBM. 2023. Retrieved March 22, 2024.
- 6. ”Understanding Denial-of-Service Attacks“. CISA. February 1, 2021. Retrieved March 25, 2024.
- 7. ”Understanding Voice over Internet Protocol (VoIP)“. (PDF). CISA. 2009. Retrieved March 25, 2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.